Phishing

Phishing is very popular among fraudsters because it takes very little effort to write a phishing email. In most cases, the email asks you to pay a bill or change a password. Everyone receives emails like this, and they are commonplace, but how can you tell whether an email is genuine or a phishing attack?
Example of a Phishing email:
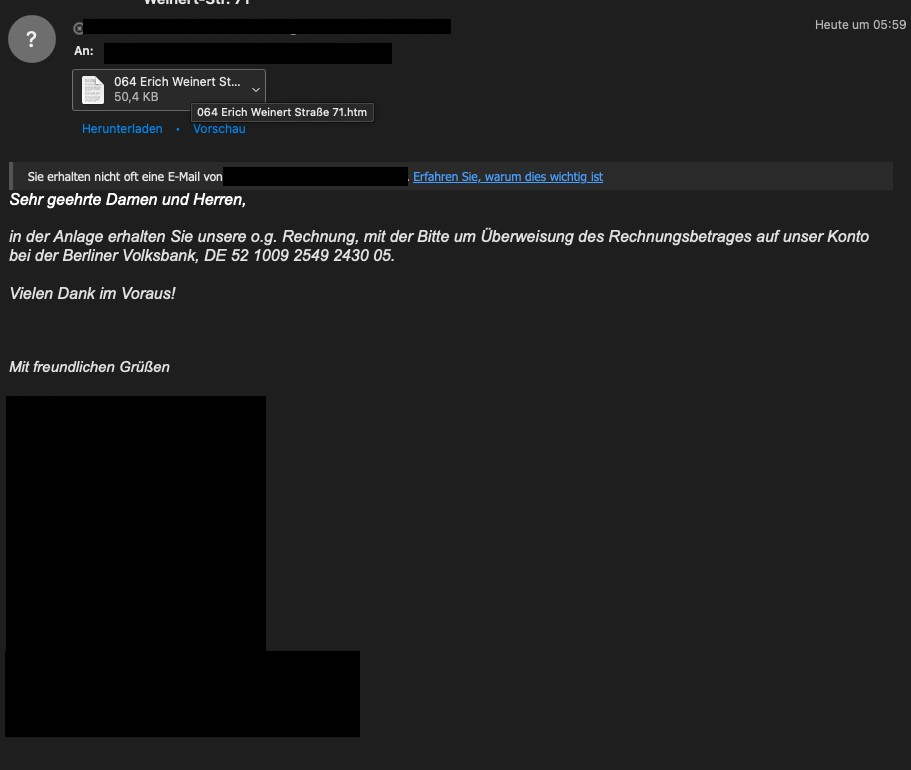
This example is a very well-crafted phishing email that is difficult to identify as a phishing attack. Only if you have never had any dealings with the company that sent the email will it be clear that it is a phishing email.
Types of phishing:
Whaling
- Focus on high-ranking individuals in an organization (management, CFO, CTO, etc.)
- Highly personalized, well researched, and has high financial or operational goals
- Often linked to specific events (quarterly financial statements, vacation replacements, etc.)
Spear-Phishing
- Attackers target specific organizations and individuals
- Messages are customized to inspire trust
- The person’s rank is irrelevant
Smishing
- Also: SMS phishing
- Attackers use SMS messages to trick victims into revealing sensitive information or clicking on malicious links
- Exploit trust in banks, delivery services, parcel notifications, government agencies, or well-known services
Protection against phishing
Whether it’s Whaling, Smishing, or a normal Phishing email on your private computer, the consequences and impact of a successful phishing attack can be devastating. For example, a well-planned and prepared phishing attack could allow a hacker to access your credit card details or even confidential company sales figures. It’s hard to imagine the consequences that each of these scenarios could have.
How to protect yourself properly
- Do not disclose confidential information or passwords.
- Check suspicious emails thoroughly.
- Be vigilant and always on your guard.
Recognizing a Phishing attack
The difficulty with phishing attacks lies in recognizing the right emails as phishing emails and blocking them. The techniques used by attackers are constantly evolving and are becoming increasingly difficult to distinguish from normal emails. Anyone can send a simple phishing email, but usually hundreds or even thousands of such phishing emails are sent out to catch multiple people.
Characteristics of a Phishing email
- Faulty texts: The email text seems very impersonal and contains spelling or grammatical errors. (However, with the increased use of AI, such errors are becoming less common, which is why this feature is becoming less relevant.)
- Reason: The email conveys a high degree of time pressure – e.g., through phrases such as “act now,” “urgent,” or the mention of a close deadline. The urgency is emphasized several times in order to prompt the recipient to act quickly and without consideration.
- Unusual address: The email comes from an unknown or suspicious address – often with an unusual domain or typos. Sometimes it is also claimed that the message comes from a large company that does not normally send sensitive information by email (e.g., government agencies, banks, corporations).